Something about commercial VPN services : What is a VPN ?

Last years, I’ve wrote a vulgarization article about the differences between a VPN and a Proxy (article in French). You may have noticed that the commercial VPN services are a common sponsor for the so-called social medias influencers. I have myself received various offers from various affiliation managers (I’m an influencer, yeay ! \o/) and I never answered them. Mostly because they simply didn’t read my contact page where I say it’s unnecessary to reach me for these kind of proposition. It’s not rudeness, au contraire, I don’t want to waste their time.
As I’m a privacy concerned person, I’ll formulate a clear statement : I will never recommend any commercial VPN service.
Like I’ve said in the previous article, I won’t prevent or dissuade you to use them. I’ll just explain in a more detailed way why I don’t trust them.
This article will be in two parts. The first one, this one, will remind and detail a little more what is a VPN and what are the VPN services offer. The second one will be an explanation of my concerns about these services.
What is a VPN
Let’s draw a basic Internet schema. In this drawing, we have a client, residing in its own Local Private Network, connected to the Internet through its gateway (usually the ISP’s router). On the other side, we have a remote server, also in its own Local Private Network, with also a Gateway.
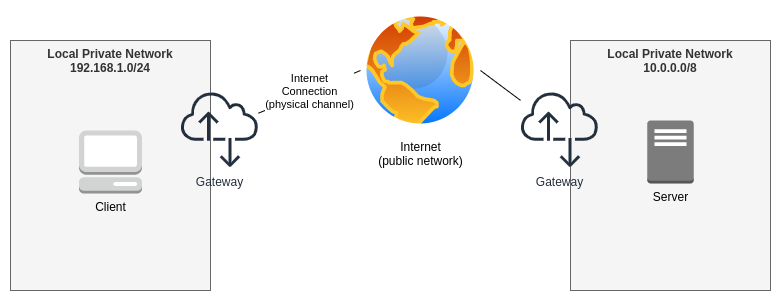 A basic Internet schema
A basic Internet schema
If Client want to reach Server’s resource, it won’t be able to communicate. By definition, a Private Network cannot be routed to the Internet or reached from there. Client or Server can go out to the Internet from their own Private Network, thanks to the Gateway, but a computer inside a private network cannot be reached from the public unless it would be exposed by a service that possesses a public IP address to expose.
A VPN, for Virtual Private Network, is a client-server protocol establishing a “direct” secured link between two privates networks. The link is virtually direct, because you still use the same physical interconnections, but at the software level, it’s the same as being locally connected to the network. By secured, I mean the tunnel is usually encrypted from the client to the server, so if anybody would try to capture the packets and read them, they won’t be able understand without the decryption key.
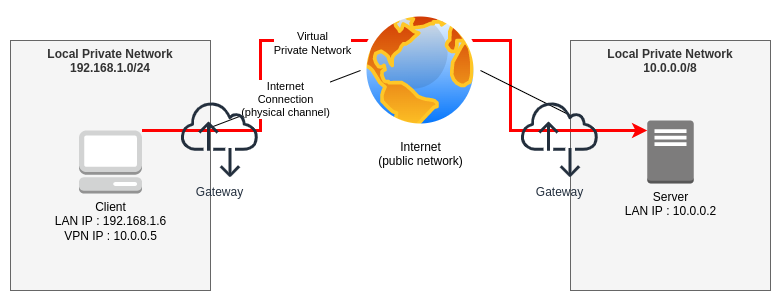
This diagram is also overly simplified, the VPN server is not displayed. It's an Internet-exposed service than can route the request to the private network. In this schema, let's assume the VPN is exposed by the Gateway which possesses a Public IP.
When a VPN is activated, the client initiates a connection to a publicly reachable server. The server authenticate the client and give it an IP, the client is connected in the same way as if it was inside the server’s Private Network.
In the diagram, I’ve added a new information : The client and server IP. As you can see, the Client has a 192.168.1.6 address corresponding to the available range of its local area network. But, when the VPN is mounted, it obtain an additional IP address which is 10.0.0.5, similar to the Server’s local area network. Both of these IP ranges are private network, so they’re impossible to route over the Internet. However, as the VPN provides routing tables to the Client, this one would know how to reach the Server’s resources.
For example, let’s admit our server is hosting an Intranet website accessible from https://10.0.0.2. If the Client tries this address without the VPN enabled, it will fail with an “Unreachable network” error. This error means that the Client has no routing table allowing it to reach he 10.0.0.0/8 network. By default, the Client will route the request to the Gateway, but as the private network IP cannot be routed to the Internet, the Gateway won’t be able to help and fail.
When the VPN is mounted, the Client’s routing table is extended with an entry saying to use the VPN’s gateway to reach the 10.0.0.0/8 network.
Don’t throw me your hammers, that’s a very simplified diagram made to understand and illustrate the principle. An actual enterprise VPN implementation is a little more complex.
So basically, if you want a simple definition of a VPN : it’s a protocol establishing a virtual direct link between two privates networks across one or more other networks, allowing the clients to reach the resources to the targeted private network without being physically inside and without requiring to expose these resources on the Internet.
What is the difference with the commercial VPN
If you’ve already read a commercial VPN offer, you may asking yourself if we’re talking about the same thing. And you’re right, despite using the same technical base, the VPN services are always talking about privacy and censorship.
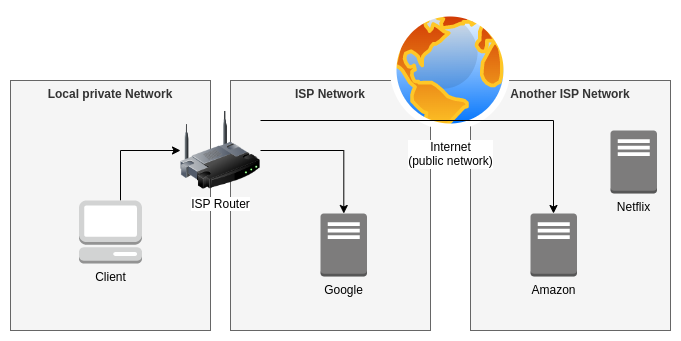
In a traditional way, when the Client wants to reach an Internet service, let’s take Google or Amazon for example, the request is going out through the Gateway (which is here the ISP router), crossing the ISP network, and if the service is hosted by another ISP, the interconnection between the various providers is used to reach it.
When the commercial VPN is mounted, a direct link between the Client and the Service network is established. The VPN Client routes all Internet trafic through the VPN Service and that’s the service endpoint which is actually establishing the connection to the Internet Service.
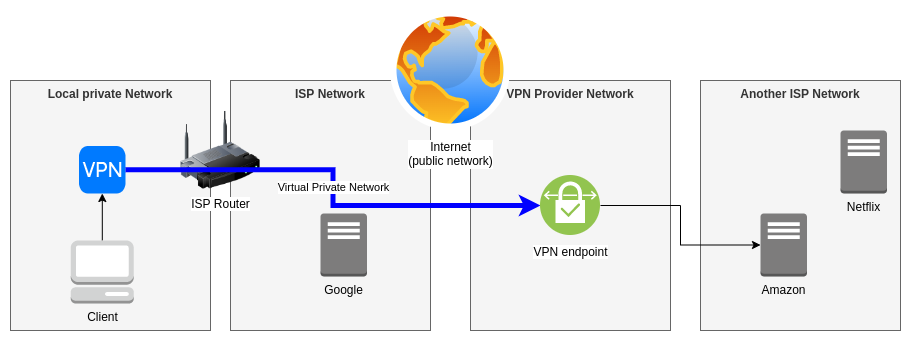
Basically, what does this mean ? You’re actually using the Internet connection of somebody else. If I want to extremely simplify the idea, that’s the same as if you were using your neighbor’s Wi-Fi to go on the Internet, the Service will see their IP and not yours.
So, when a commercial VPN propose you to access resources that are not usually reachable from your geographical position (common example : seeing US Netflix catalog from France), the VPN client will establish a connection to an endpoint that is physically in the USA. And Netflix will see the endpoint’s IP, not yours, and will believe you’re in USA and not in France. That’s because the countries IP addresses blocks are well known, that’s what we call Internet geolocation from the client’s IP address.
In which cases a VPN is mandatory ?
The VPN are commonly used at enterprise level. Basically for allowing their employees to remotely access the company resources without exposing them on the Internet. If you’re remotely working from your company, you may possibly use one unless all of your enterprise tools are themselves SaaS services. For example, if you’re company hosts its own Mail server, you may require a VPN to access it. However, if its mail service is hosted my Microsoft 365 or other, as it’s a Web service you won’t need any VPN.
A VPN is also a useful tool to protect the client from unsecured public networks, like public Wi-Fis, or untrusted networks, which can possibly collect or trace the users activities using Man in the Middle attack pattern.
VPN services are also used in countries where the Internet is highly restricted and censored to bypass it. In these countries, the VPN are usually forbidden or restricted to a Government-approved list of operators. This use case is mostly used by journalists or activists, with the risk that may occur.
What are the commercial VPN proposing ?
For the requirements of this article, I’ve randomly chosen five VPN services based on the common names I’ve heard, taken from a random “VPN comparison” search result on the web, or the one who sent me their affiliation propositions with no actual criteria. As I don’t really care about these services, I can’t establish a sorting, and I honestly don’t care about this. My goal is to compare what do they propose.
I won't name any of them here to avoid free advertising.
So please, don't ask 🙏
These providers ads have usually the same arguments :
- “Online privacy protection”
- “Security”
- “Anonymous surfing”
- “Hiding your IP”
- “Fast bandwidth”
- “Global worldwide coverage”
- “Supports multiple device”
- “No user tracking”
- “Freedom”
- “Independently audited”
The commercial website have the standard presentation. What is a VPN, the benefits of using their service, the anxiety-provoking speech, and of course, they have the solution. A list of famous newspapers (New York Times, Forbes, The Guardian, etc) as a social proof. We are in the common rules of any “well being” oriented product. I’ve usually noticed a top banner on the websites showing my IP and a very worrying “Unprotected” word displayed in bold red characters.
😱

Oh no ! They can see a public information !
Ok, I must admit I’m a little sardonic, but these kind of commercials always make me smile.
While browsing these websites, I’ve seen some common contents in the quick access links. Here is a non-ordered list :
“What is a VPN ?”
These services’ definition of VPN has some common items :
- A service that protects your Internet connection and privacy online
- A service that protect you from online tracking, interference and censorship
- A service that reroutes your online trafic to an encrypted tunnel
- A service that makes your browsing private
And the most used part : “a service that hides your IP”.
If your read the definition I’ve made above, you can see its more a consequence of the VPN usage than its basic design purpose. Some of these items true and are actually benefits offered by the usage of a VPN, others are extrapolation or just false assertions. This will be developed in the next article. Here, I’ll just list the items with no judgment.
“Secure and Freedom”
They are the two most used words on these websites. With their VPN, you will be “secure” and you can enjoy the “freedom”.
According to most of the providers I’ve seen, a VPN should protect the user of ads, tracking, or malwares.
“Privacy and no-logs policy”
Another widely exposed benefit of using their service is to protect your online privacy, mostly thanks to the previous “security” item.
One of the point is related to a “no-log policy”, which mean they don’t log their users activities so no Governments or authorities would be able to have these data from them.
“Fast servers”
That’s another common argument of the VPN services : they all have fast servers around the world. Why do they need to say that ?
Usually, a VPN is slow. Not by design, but that’s just because you’re using a centralized access and routing all of your Internet trafic through it. So a usual VPN (like the one you could use while working from home) can have limited resources because the bandwidth can quickly be an expensive resource. As one of the use cases of the VPN services is to access geo-restricted content, they have to provide a decent bandwidth.
“Independently audited”
Of course, every commercial VPN service are talking about security, privacy, no-logs, etc. And to “prove” that, they expose an argument from authority : “we’ve been audited by an independent third-party” or they invite auditors and testers to review their privacy policy.
So far…
For the first part of this article, I’ve reminded and explained what is a VPN as a protocol. Then, I’ve just read some random VPN services commercial websites and noted the usual arguments and benefit they expose. In the next article, I’ll expose my personal concerns about these services and why I don’t trust them.